Intranet access restricted due to cyber attacks
photo courtesy of Thomas Jefferson High School for Science and Technology
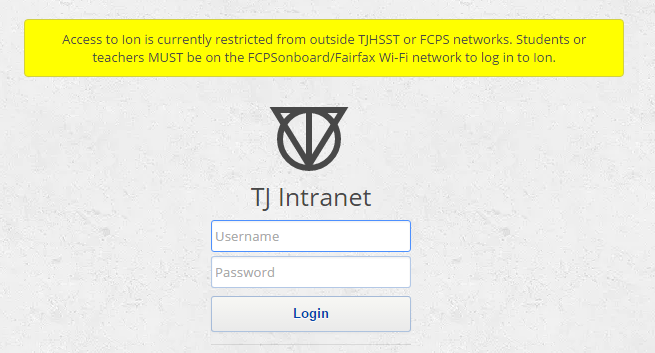
Intranet access is currently limited to logging in on school grounds and using Fairfax County WiFi. The restriction began on May 27.
June 9, 2016
Intranet, Jefferson’s online platform for students to sign up for eighth period blocks, has been temporarily blocked due to external cyber attacks. Some information from the site’s student directory became vulnerable during the breach, and restrictions on access to the site were put in place on Friday May 27. Students and staff can now only use the site on school grounds, using Fairfax County WiFi.
Four student network webmail accounts were accessed, which allowed the attacker to view the personal information of about twenty students associated with the accounts. This information may have included email addresses and phone numbers.
“The attacker was able to ‘become’ a few TJ students in terms of their online accounts,” senior and lead SysAdmin James Woglom said. “They were able to access some directory information that students voluntarily made public with their privacy settings, but did not access any student files or other private information.”
Since the attacks, the SysAdmin team has put in place several preventative measures in order to prevent future attacks, including locking down the affected accounts as well as limiting access to the site.
“Immediately once we learned that student accounts had been compromised, we locked their accounts so they couldn’t be logged into,” Woglom said. “Soon after, we locked external access to the TJ Intranet and our access servers, which are the only methods that an attacker could use to log into and access our infrastructure.”
Ongoing investigations are working to uncover the identity of the attacker as well as the means they used to attack the database. The security breach is suspected to have been caused by students using the same passwords for many sites, making their accounts vulnerable to attack.
“We believe that the way the accounts were compromised in the first place was by students reusing their password across multiple services,” Woglom said. “We suspect that the attacker or attackers found people’s personal credentials, like email passwords, in large data security breaches. They then tried to guess [those passwords] for Intranet accounts.”